1. Overview
This document provides a more detailed and technical description of the challenges involved in configuring a network of FRP replication servers “on top” of a users network topology.
FRP is designed to accommodate a variety of network configurations and several sample scenarios are described here in detail:
- A basic LAN configuration (all servers inside the same firewall on the same LAN, see section 3)
- A LAN with remote servers (some servers outside the firewall, see section 4)
- A mixed configuration (more than one LAN, separated by a WAN, each with their own firewalls, see section 5)
2. Configuration
2.1 What needs to be configured?
To allow FRP servers to cooperate in executing and monitoring replication jobs, the following needs to be established:
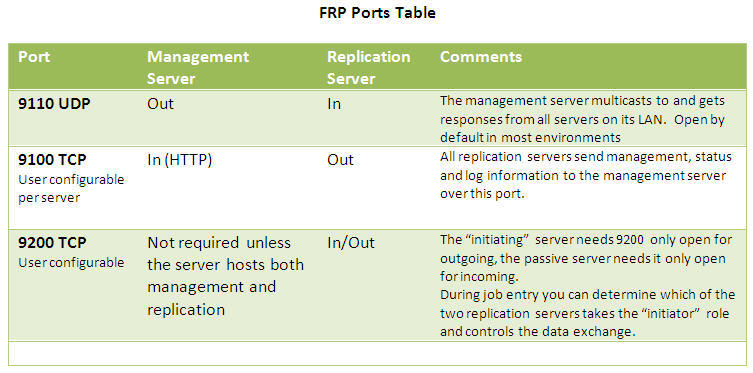
- Discovery: The management server needs a list of servers that participate in the FRP network. FRP servers residing on the same LAN as the management server are auto-discovered using a UDP multicast over port 9110. Remote servers need to be added manually via the management console.
- Management Server Access: Each replication server needs to be able to communicate with the management server over port 9100. This connection is mainly used to:
- Send status and log information’s from the replication servers to the management server.
- Collect and distribute configuration and job information
- Establish initial membership in the FRP network
- Monitor Online/Offline server status
- Management Server Console Access: The management console application is a web server running as part of the management server. Local or remote desktops need to reach this server over the same port, 9100, using the HTTP protocol.
- Replication server Access: Each replication server needs to be able to communicate and transfer data to and from other replication servers over port 9200.
- Mail Access: The management server can be configured to send alert emails to the administrator. This simple configuration is not discussed here.
FRP provides the tools for discovery. Local servers can be automatically discovered and remote ones can be manually added by the administrator as will be described below.
The network administrator, using the network hardware and tools configures the required access. This often involves tasks such as opening ports on firewalls, port forwarding or VPN tunneling.
While a full discussion of network configuration is beyond the scope of this document, the examples below will highlight some key tasks and point out areas where FRP is designed to assist in establishing and maintaining a functioning replication network.
2.2 How are the ports used?
Below is a table listing the ports used by FRP management and replication servers and how they should be opened in the firewall(s) controlling access to these servers.
2.3 Where is the configuration stored?
The main repository of configuration information is stored in an xml file named configuration.xml in the frp/etc directory (i.e. under the FRP main installation directory). Information about all the FRP servers, their role, ip addresses, host names and more is stored in this file. All replication job definitions are also stored there.
The configuration file is maintained by the management server. Any configuration changes, whether auto detected or user entered result in a revision to this file. The revised configuration xml is then propagated to all replication servers.
It may be worth noting that a replication server does not need to be connected to the management server to perform its jobs. All replication servers read and schedule their jobs independently using their local copy of the configuration file.
In addition to the main configuration file, FRP maintains server specific settings such as timeout thresholds, memory allocation and other specialized parameters are also maintained in the frp/etc directory. Most of these settings can be set in the Advanced Server Properties page of the management console. Please make sure not to tamper with or delete files in this folder.
3. Example: Basic LAN Configuration
The simplest configuration for an FRP network is one where all servers are on the same LAN.
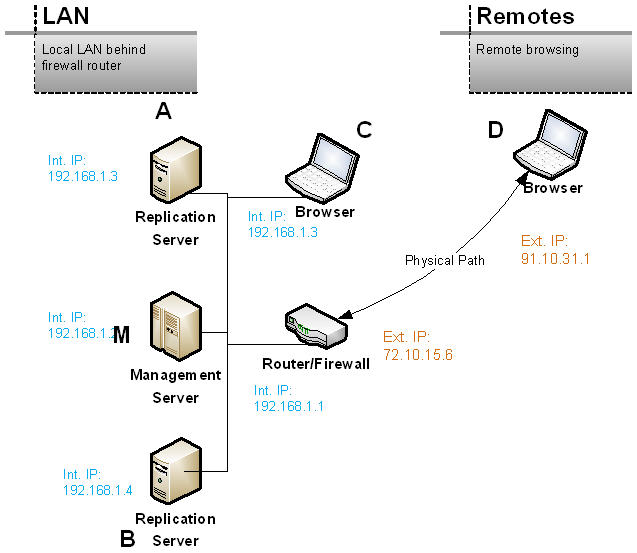
In this sample scenario, the management server M and two other replication servers A and B are on the same internal LAN behind a router and firewall. An additional desktops (or laptop) C is used to run a browser and connect to the management server M via the FRP Management Console. The desktop C is on the same LAN. Note that M can also host a replication server.
3.1 Server Discovery and Addressability:
The management server M will automatically discover servers A and B. After installing FRP on M and starting the management server, for auto discovery to function, you have to install FRP and start it as a replication server (only) on servers A and B. Every new server you might add to the LAN and install FRP on, will be automatically discovered and added to the FRP configuration.
The management server M and replication servers A and B can easily connect to each other using the internal LAN ip addresses. Normally, other than opening the relevant ports, no additional user action is required. This is also true for the desktop C. It can access the management console by typing in the URL: http://192.168.1.2:9100/
However, for Browser D outside the firewall, to access M, you must use the external ip address of the router/firewall and then rely on internal routing, such as forwarding port 9100 to M, to establish a connection from D to M. This is described in more detail in the next section.
3.2 Procedure
Installation
- Install FRP on all servers. Make sure to indicate “Management and Replication” or “Management Only” for M. All other servers should be installed as “Replication Server Only”.
- Have the installer start the application on each server. From your browser, connect to the management console and select “Servers” to bring up the Servers Overview page.
- Normally, all the replication servers on the LAN will be auto discovered and will appear in the servers list. If they do not, you may need to open firewall port 9110 for UDP on all servers. (Most internal Windows firewalls have UDP open by default. The Advanced Windows firewall has UDP blocked in some configuration i.e. Windows 7)
Internal Firewall setup
- If your server runs an internal firewall, open TCP ports 9100 and 9200 for both incoming and outgoing traffic.
- Also verify that the firewall allows UDP traffic by default; otherwise open port 9110 for UDP packets bi directionally.
- These steps should be repeated for every server (i.e. servers M, A and B and desktop C).
Firewall/Router setup
- On the LAN’s router/firewall, forward incoming port 9100 to M. See more detail about port forwarding in the next section.
- This step is not required unless you want to access the management console on M, via browser D, from outside the firewall.
4. Example: Mixed Configuration – A LAN with Remote Servers
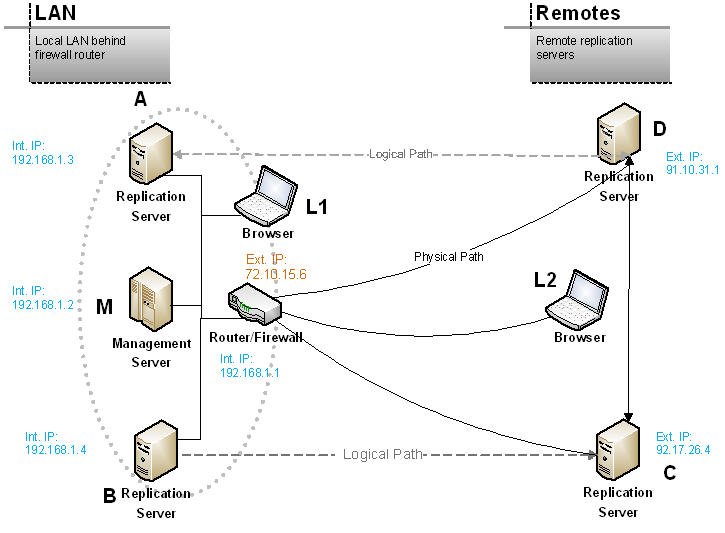
In this scenario, the management server M and two other replication servers A and B are on the same internal LAN behind a router and firewall. Two additional remote replication servers, C and D are “outside” and have each their own static external ip address. Laptops L1 and L2 are connected, one inside the firewall and one outside, neither have a static ip address.
4.1 Server Discovery and Addressability:
The management server will automatically discover servers A and B. You will have to manually add servers C and D to the configuration using the management console or the command line interface. See section 3.1 above for more details.
4.2 Basic Routing
To describe how servers C and D can communicate with M, A and B who are behind the firewall (as well as how L2 can access the console on M), we’ll first provide a brief description of basic routing and how FRP is configured to support it.
4.2.1 VPN/Tunneling
In this scenario the remote server looks to the other servers on the LAN as if it is local and has a local ip address on the same subnet as the management server. From an FRP perspective, the remote server behaves like a local one with one exception. In most scenarios, the remote server will not be reached by a multicast and not be auto-discovered, you will need to add it manually with its “local” ip address. So in our above examples you will need to add C and D to the configuration via the management console and specify (in the Add Server page) the ip addresses assigned to them by the VPN/tunneling. L2 is not a replication server, so there is no need to configure it. It will be able to access M locally.
4.2.2 Port Forwarding
Remote replication servers (C, D) are not auto discovered and have to be added to the configuration by the administrator using the management console. To access the management server, a remote server connects to the external ip address of the management server.
Two scenarios are very common. In one, the management sever is addressable, that is, it has been assigned a static external ip address. Other than opening the relevant ports (see 2.2) throughout the path to M, no additional routing is required and no extra FRP configuration is required.
In the other common scenario (depicted in the diagram above), M does not have its own external static ip address. Instead, an external ip address is assigned to the router/firewall connected to the internet or the WAN. When C attempts to connect to M it supplies the address 72.10.15.6 which reaches the router/firewall. To get from there to M and complete the desired path, port forwarding rules are commonly used. In our case, an incoming connection request to port 9100 (colloquially referred to as incoming port 9100) is routed to the management server’s local ip address (192.168.1.2).
Note that by implementing this forwarding rule on your router, you also allow D and L2 to communicate with M as well as any other remote server you might install FRP on in the future.
If M also hosts a replication server, route incoming port 9200 to M’s local ip address and you can now perform data replication between C and D from outside the firewall and M inside.
How will other “internal” replication servers, behind the router/firewall (A and B), communicate with our remote replication server (C and D)?
The direction of a connection is a key factor in routing. When a server is behind a firewall, it can still initiate a connection out to any known server (provided the needed ports are open). Port forwarding is only needed for incoming connections, from a remote server to an internal one. In our scenario, no routing is needed to allow A to establish an outgoing connection to D, but if D wants to establish an outgoing connection to A, the connection request comes into the router/firewall and needs to be routed to A.
By selecting the internal servers as the initiators of replication, you can run replication jobs between A and D with no further routing. You tell FRP, when you create a replication job between A (internal) and D (remote), that A is the “initiator”. By doing so, you actually define the direction of the connection as “outgoing” from A, the internal server behind the firewall, to D, the remote server. Therefore no routing is required.
Note that designating a server as the initiator is independent of which server is the source or destination in the job. Source or destination simply tells FRP the directory data is copied from and the one data is copied to. The server that initiated the connection and controls data replication could be either one. By default, FRP would assign the initiator role to the source server, but you can switch roles when convenient. Whenever one server is behind a firewall and the other has an external address, designate the server behind the firewall as the initiator to avoid having to do any port forwarding.
What if the remote server is behind its own router/firewall?
Please see the next section about multiple LANs.
4.3 Procedure:
Installation
- Install FRP on all servers. Make sure to indicate “Management and Replication” or “Management Only” for M. All other servers should be installed as “Replication Server Only”.
- Have the installer start the application on each server. From your browser, connect to the management console and select “Servers” to bring up the Servers Overview page.
- Normally, all the replication servers on the LAN (i.e. A and B) will be auto discovered and will appear in the servers list. If they do not, you may need to open firewall port 9110 for UDP on all servers. (Most internal Windows firewalls have UDP open by default. The Advanced Windows firewall has UDP blocked in some configuration i.e. Windows 7)
- Add servers C and D to your configuration using the Add Server page. Accept the default port number (9200).
Internal Firewalls setup
- If your server runs an internal firewall, open TCP ports 9100 and 9200 for both incoming and outgoing traffic.
- Also verify that the firewalls allow UDP traffic by default; otherwise open port 9110 for UDP packets bi directionally.
- These steps should be repeated for every server on the LAN (i.e. servers M, A and B and desktop C).
Firewall/Router setup
This is only required if servers C and D are not tunneled/VPN’d. Our objective is to route incoming connections for port 9100, directed at the management server, to M. A secondary goal, if M also hosts a replication server, is to route incoming connections for port 9200 to M as well.
FRP Job setup:
For replication jobs between a remote server (C or D) and a local server behind the firewall (A or B) you need to mark the local server as the “initiator” in the Advanced Job properties panel.
No special settings are required for any other jobs. See section 4.2.2 for a detailed discussion.
5. Example: Mixed Configuration – Multiple LANs
In this scenario, you have two offices each with its own LAN and router/firewall and each with servers residing behind the firewall. In office #1 you have the management server M and two replication servers, A and B, on the same internal LAN behind a router/firewall F1. In remote office #2 you have two additional replication servers, C and D on an internal LAN behind router/firewall F2. Only routers F1 and F2 are assigned an external ip address. All other servers have only internal ip addresses on their respective LANs.
Additionally, laptops L1 and L2 are connected to their local LANs, each behind its respective router/firewall; neither have a static ip address. Both are intended to be used to access M’s management console via a browser.
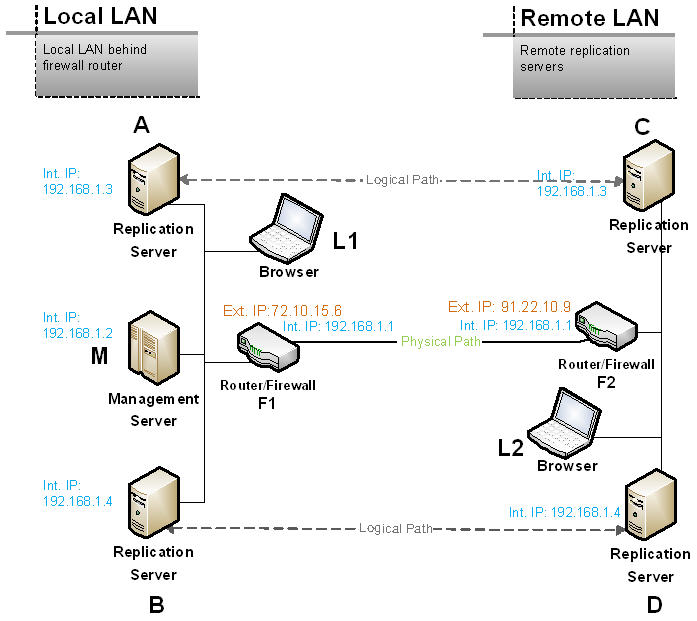
This scenario extends the previous scenario discussed in section 4 by placing servers C and D and laptop L2 behind a firewall (F2) where they only have an internal LAN ip address.
5.1 Server Discovery and Addressability:
The management server will automatically discover servers A and B. You will have to manually add servers C and D to the configuration using the management console or the command line interface. See section 3.1 above for more details. Servers C and D will be added using F2’s ip address and custom port numbers as described below.
5.2 Routing
A description of routing for a simpler scenario is provided in section 4.2. This new scenario adds a couple more challenges.
Reaching Servers C and D
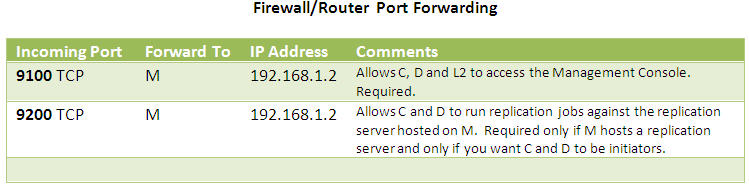
To be able to add servers C and D to the configuration, the management server M must be able to establish a connection, over the replication port (9200 by default) to these servers. Since the servers C and D are behind firewall F2, all M can use is the router’s ip-address. To get from F2 to C or D, we need to route the connections inside the firewall from F2 to the target servers.
We therefore configure replication server C in FRP to use port 9201. It will listen for incoming connections from other FRP replication servers on this port. We forward port 9201 on F2 to C’s local ip address (192.168.1.3). As a result, the management server M, as well as any other replication server, even those behind firewalls, can reach C by using F2’s external ip address (91.22.10.9) and port 9201. Note that once you add C to the configuration with port 9201 and you forward port 9201 to C, FRP will take advantage of the setup and the rest of the connection and replication process is automatic.
Similarly, configure D to use port 9202 and forward that port on F2 to D’s local ip (192.168.1.4). Also note that the custom port numbers (9201,2) are arbitrary.
Reaching Servers M, A and B
To reach M, forward ports 9100 and 9200 on F1 to M. A and B do not need to be reached. Instead, for jobs involving A or B with a remote server such as C or D, define A and B as initiators so they instead connect out to and reach C and D. This is described in detail in section 4.2.2.
5.3 Procedure:
Installation
- Install FRP on all servers. Make sure to indicate “Management and Replication” or “Management Only” for M. All other servers should be installed as “Replication Server Only”.
- Have the installer start the application on each server. From your browser, connect to the management console and select “Servers” to bring up the Servers Overview page.
- Normally, all the replication servers on the LAN (i.e. A and B) will be auto discovered and will appear in the servers list. If they do not, you may need to open firewall port 9110 for UDP on all servers. (Most internal Windows firewalls have UDP open by default. The Advanced Windows firewall has UDP blocked in some configuration i.e. Windows 7)
- Adding servers C and D to your configuration is deferred till after the router/firewall setup.
Internal Firewalls setup
- If your servers runs an internal firewall, open TCP ports 9100 and 9200 for both incoming and outgoing traffic.
- Also verify that the firewalls allow UDP traffic by default; otherwise open port 9110 for UDP packets bi directionally.
- These steps should be repeated for every server on the LAN (i.e. servers M, A and B and desktop C).
Firewall/Router setup
Forward the ports as per the table below.
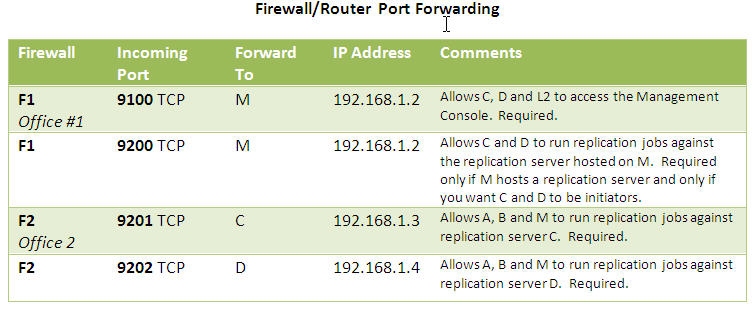
Forward the ports as per the above table.
Adding Servers
- You must complete the Firewall/Router setup for F1 and F2 before undertaking the Add Servers procedure
- Add server C to your configuration using the Add Server page. For its ip address, enter F2’s external ip address (91.22.10.9). For port number, assign C custom port number 9201 and save.
- Add server D to your configuration using the Add Server page. For its ip address, enter F2’s external ip address (91.22.10.9). For port number, assign D custom port number 9202 and save.
FRP Job setup
For replication jobs between a remote server (C or D) and a local server behind the firewall (A or B) you need to mark the local server as the “initiator” in the Advanced Job properties panel.



